Protection at all levels
Embedded
Cyber Security
Detecting and Mitigating Threats
Embedded Cyber Security for Complex Electronics
At the heart of our work lies a comprehensive security approach aimed at identifying and mitigating risks. Through precise vulnerability analyses and the implementation of security mechanisms, we make systems resilient to threats. We focus particularly on securing communication pathways, protecting sensitive data, and enhancing the robustness of hardware peripherals. For us, cyber security is more than just protective measures—it is a thoughtful process that accompanies the entire lifecycle of the product.
Core elements of our embedded cyber security activities include:
Vulnerability Analysis: Identifying and assessing potential security gaps in software and hardware.
Threat and Risk Assessment: Systematic analysis of potential threat scenarios and risk assessments to develop targeted countermeasures.
Authentication and Authorization: Verifying all access to ensure that only authorized users or systems have access.
Secure Updates: Ensuring that only authorized and verified software updates reach the devices.
Encrypted Communication: Protecting data transmission through proven encryption methods.
Key Management: Securely managing cryptographic keys and secrets throughout a product’s lifecycle.
Robust Peripherals: Securing and hardening hardware components against physical and electronic tampering.
Secure Storage: Protecting sensitive data through secure storage management and access control.
Trusted Platforms: Building secure platforms that provide essential trust anchors for device cyber security.
Modern Cyber Security Technologies
We rely on the latest technologies and tools to ensure comprehensive protection for embedded systems. Our approach combines industry standards with innovative security mechanisms to meet even the most demanding cyber security requirements. The foundation of our work is a robust blend of software and hardware solutions designed to meet the highest security standards.
-
AES (Advanced Encryption Standard)
-
CMAC (Cipher-based Message Authentication Code)
-
SSH (Secure Shell)
-
TLS (Transport Layer Security)
-
Diffie-Hellman Key Exchange
-
RSA (Rivest–Shamir–Adleman Encryption)
-
ECDSA (Elliptic Curve Digital Signature Algorithm)
-
TRNG (True Randon Number Generators)
-
HMAC (Hash-based Message Authentication Code)
-
ECC (Error Correction Code)
-
ARM TrustZone
“”
Cyber resilience is not a state but a process. Taking it seriously must now be part of responsible business practice.
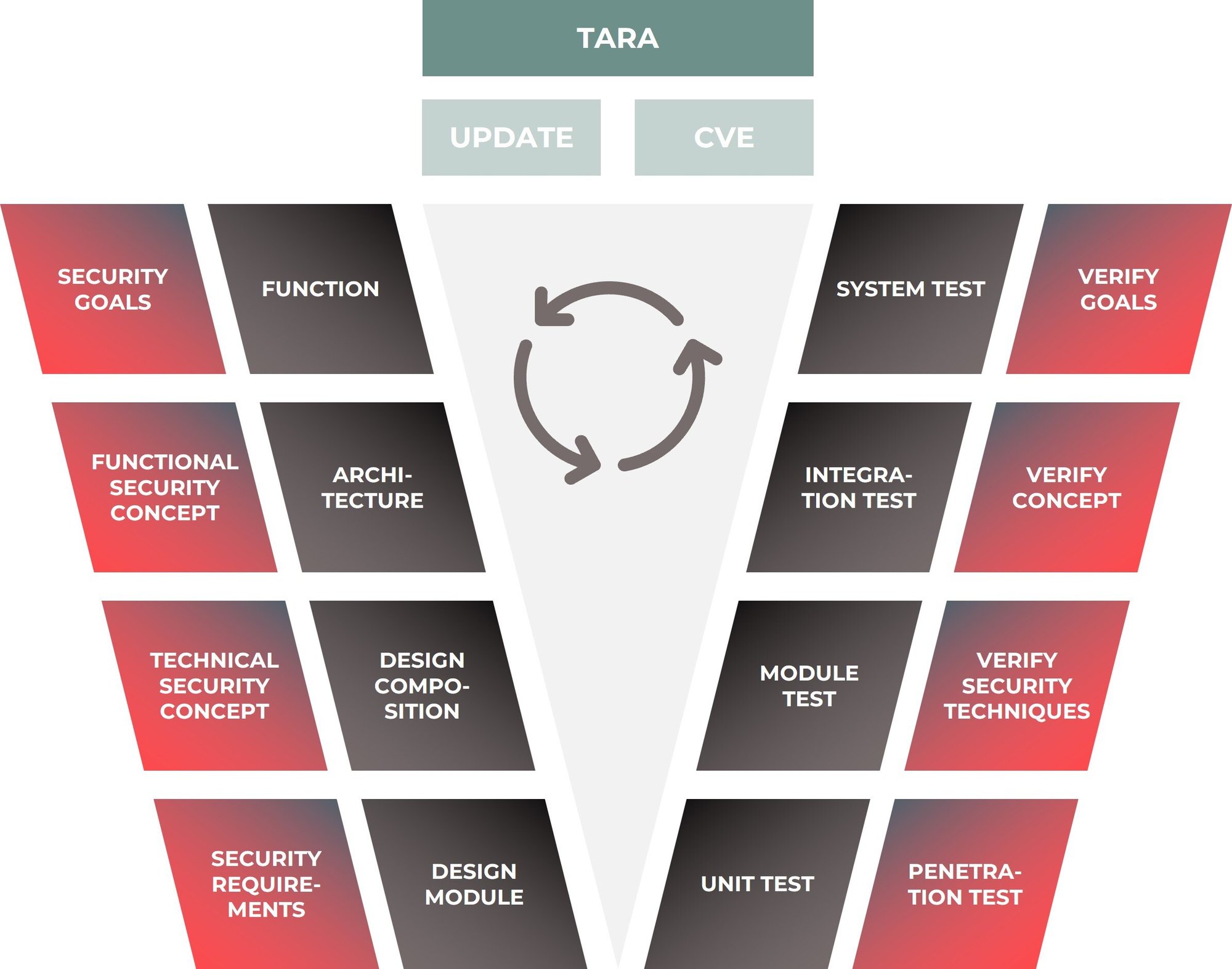
Process-Oriented and Regulatory-Compliant Security
Our cyber security solutions are developed within a structured framework and meet all regulatory requirements. Through an organized approach, we ensure that our solutions are not only technically sound but also normatively compliant. Our multi-layered security strategy covers all aspects of cyber security, guaranteeing that our clients consistently receive well-secured embedded systems.
Our services include:
CURIOUS?
Questions, comments, or suggestions about how we work and develop? We are happy to answer them in a personal conversation. Feel free to send us an inquiry about your concerns.
We look forward to hearing from you.

Dr. Hendrik Schnack
Sales, Technology

Hummam Kadour
Account Management